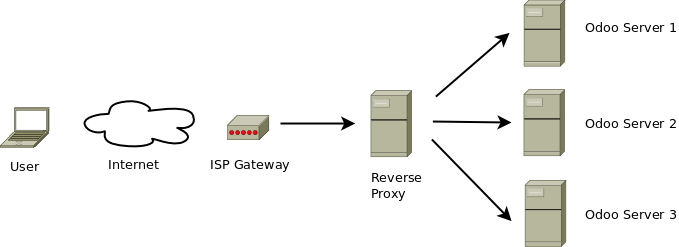
A solution


Install Nginx using Debian Package system
sudo apt-get install -y nginx nginx-common nginx-coresudo mv /var/www/html/index.html /var/www/html/index-orig.html
sudo nano /var/www/html/index.html 1 <!DOCTYPE html>
2 <html lang="en">
3 <head>
4 <meta charset="utf-8">
5 <title>Default</title>
6 </head>
7 <body>
8 <p>Defaul page for server: proxy.example.com</p>
9 </body>
10 </html>Download this file: index.html
sudo nano /etc/nginx/sites-available/default 1 server {
2 listen 80 default_server;
3 listen [::]:80 default_server ipv6only=on;
4 server_name default.example.com;
5
6 root /var/www/html;
7 index index.html index.htm;
8
9 # Redirect 301 to HTTPS
10 # return 301 https://$host$request_uri;
11
12 location / {
13 try_files $uri $uri/ =404;
14 }
15
16 access_log /var/log/nginx/default.access.log;
17 error_log /var/log/nginx/default.error.log;
18 }Download this file: default
sudo nano /etc/nginx/sites-available/default-ssl 1 server {
2 listen 443 default_server;
3 listen [::]:443 default_server ipv6only=on;
4 server_name default.example.com;
5
6 root /var/www/html;
7 index index.html index.htm;
8
9 ssl on;
10 ssl_ciphers ALL:!ADH:!MD5:!EXPORT:!SSLv2:RC4+RSA:+HIGH:+MEDIUM;
11 ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
12 ssl_prefer_server_ciphers on;
13 ssl_certificate /etc/ssl/wildcard.example.com/public.crt;
14 ssl_certificate_key /etc/ssl/wildcard.example.com/private.pem;
15
16 location / {
17 try_files $uri $uri/ =404;
18 }
19
20 access_log /var/log/nginx/default-ssl.access.log;
21 error_log /var/log/nginx/default-ssl.error.log;
22 }Download this file: default-ssl
cd /etc/nginx/sites-enabled
rm -rf *
ln -s ../sites-available/default default
ln -s ../sites-available/default-ssl default-ssl
service nginx restart
Install Apache 2 in prefork mode using Debian Package system
sudo apt-get install -y apache2 apache2-utils apache2-mpm-preforkEnable rewrite and SSL modules
sudo a2enmod rewrite
sudo a2enmod sslDefine ServerName directive and ports where Apache2 will listen
sudo nano /etc/apache2/ports.conf1 ServerName proxy.example.com
2 Listen 80
3 <IfModule mod_ssl.c>
4 Listen 443
5 </IfModule>Set several directives to secure Apache
sudo nano /etc/apache2/conf-enabled/security.conf 1 <Directory />
2 Options None
3 AllowOverride None
4 Order Deny,Allow
5 Deny from all
6 </Directory>
7 ServerTokens Prod
8 ServerSignature Off
9 TraceEnable Off
10 <DirectoryMatch "/(\.svn|\.git)">
11 Deny from all
12 Satisfy all
13 </DirectoryMatch>Enable headers module
sudo a2enmod headersInstall Apache 2 ModSecurity Rules
sudo apt-get install -y libapache2-modsecurity modsecurity-crsInclude ModSecurity rules
sudo nano /etc/modsecurity/rules.conf1 <IfModule security2_module>
2 Include "/usr/share/modsecurity-crs/*.conf"
3 Include "/usr/share/modsecurity-crs/activated_rules/*.conf"
4 </IfModule>Enable Secure Rules Engine
sudo nano /etc/modsecurity/modsecurity.conf-recommended1 # SecRuleEngine DetectionOnly
2 SecRuleEngine OnEnable all base and optional rules
cd /usr/share/modsecurity-crs
for f in `ls --color=never base_rules/ | grep modsecurity`; do sudo ln -s /usr/share/modsecurity-crs/base_rules/$f activated_rules/$f; done
for f in `ls --color=never optional_rules/ | grep modsecurity`; do sudo ln -s /usr/share/modsecurity-crs/optional_rules/$f activated_rules/$f; donesudo mv /var/www/html/index.html /var/www/html/index-orig.html
sudo nano /var/www/html/index.html 1 <!DOCTYPE html>
2 <html lang="en">
3 <head>
4 <meta charset="utf-8">
5 <title>Default</title>
6 </head>
7 <body>
8 <p>Defaul page for server: proxy.example.com</p>
9 </body>
10 </html>Download this file: index.html
sudo nano /etc/apache2/sites-available/default.conf 1 <VirtualHost *:80>
2 ServerAdmin webmaster@example.com
3 ServerName default.example.com
4
5 DocumentRoot /var/www/html
6
7 <Directory /var/www/html>
8 Options None
9 AllowOverride None
10
11 # Redirect 301 to HTTPS
12 # RedirectMatch permanent ^/(.*)$ https://${HTTP_HOST}/$1
13
14 # Access control by IP or IP range
15 # Order deny,allow
16 # Deny from all
17 # Allow from 10.xx.0.0/16 127.0.0.0/255.0.0.0 ::1/128
18
19 # Allow all
20 Order allow,deny
21 Allow from all
22 </Directory>
23
24 ErrorLog /var/log/apache2/default.error.log
25 LogLevel warn
26
27 CustomLog /var/log/apache2/default.access.log combined
28 </VirtualHost>Download this file: default.conf
sudo nano /etc/apache2/sites-available/default-ssl.conf 1 <VirtualHost *:443>
2 ServerAdmin webmaster@example.com
3 ServerName default.example.com
4
5 SSLEngine on
6 SSLProtocol all -SSLv2 -SSLv3
7 SSLCipherSuite ALL:!ADH:!EXPORT:!SSLv2:RC4+RSA:+HIGH:+MEDIUM
8 SSLCertificateFile /etc/ssl/wildcard.example.com/public.crt
9 SSLCertificateKeyFile /etc/ssl/wildcard.example.com/private.pem
10
11 DocumentRoot /var/www/html
12
13 <Directory /var/www/html>
14 Options None
15 AllowOverride None
16
17 # Access control by IP or IP range
18 # Order deny,allow
19 # Deny from all
20 # Allow from 10.xx.0.0/16 127.0.0.0/255.0.0.0 ::1/128
21
22 # Allow all
23 Order allow,deny
24 Allow from all
25 </Directory>
26
27 ErrorLog /var/log/apache2/default-ssl.error.log
28 LogLevel warn
29
30 CustomLog /var/log/apache2/default-ssl.access.log combined
31 </VirtualHost>Download this file: default-ssl.conf
cd /etc/apache2/sites-enabled
rm -rf *
ln -s ../sites-available/default.conf 000-default.conf
ln -s ../sites-available/default-ssl.conf 000-default-ssl.conf
service apache2 restartEnable HTTP Proxy module
a2enmod proxy_httpOnly Root (and Root group) can access configuration files
sudo chown -R root:root /etc/apache2
sudo chmod -R o-rwx /etc/apache2Restart Apache 2 service
sudo service apache2 restartA public key infrastructure (PKI) is a set of hardware, software, people, policies, and procedures needed to create, manage, distribute, use, store, and revoke digital certificates and manage public-key encryption.
Read more at Wikipedia
Ubuntu
Other platforms
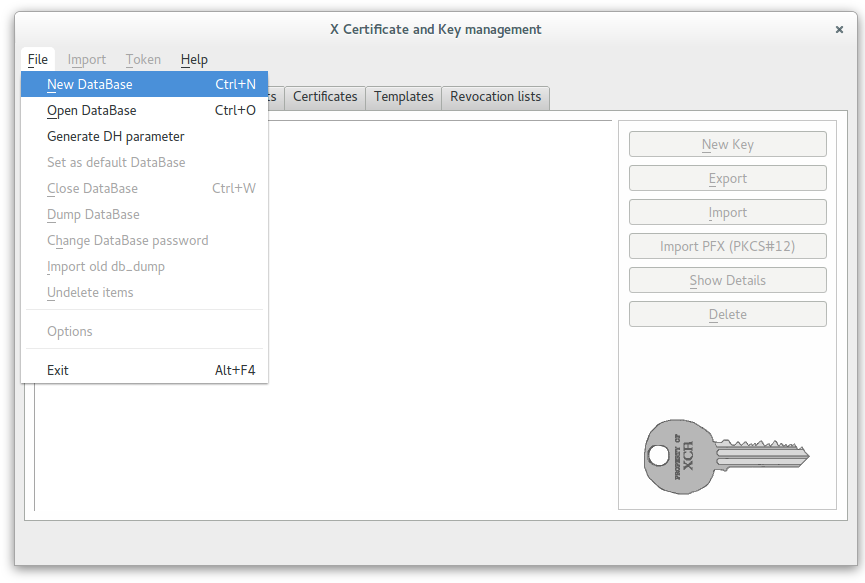
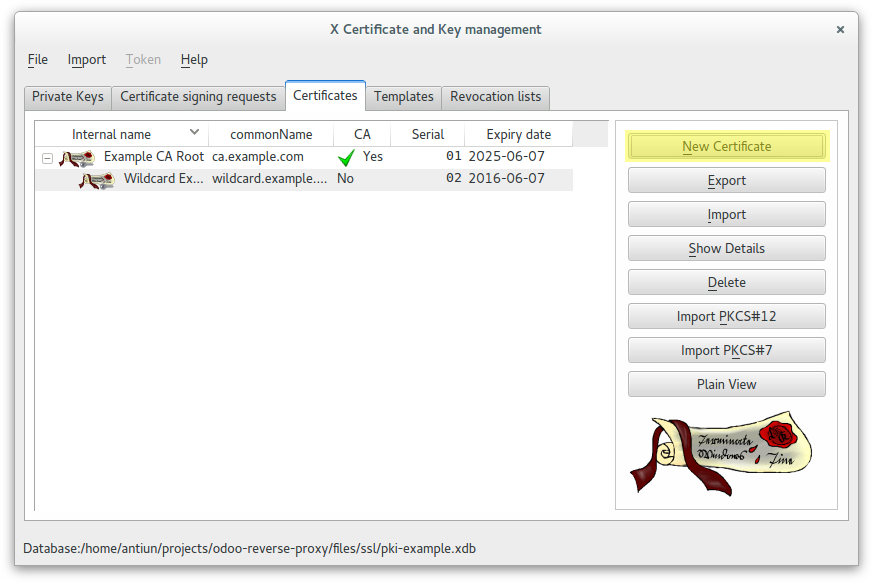
Create a new PKI database where private keys and certificates will be created
Set PKI database password
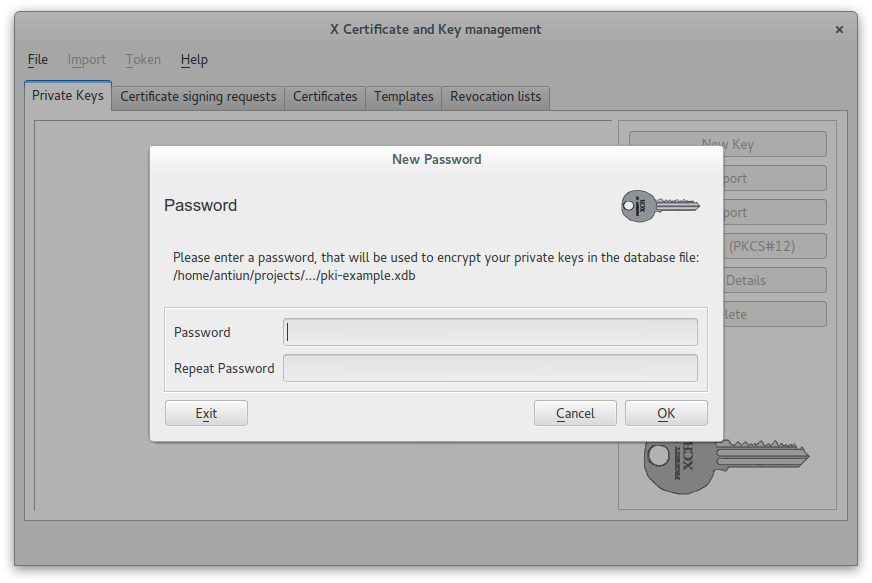
In this case we used this password: example
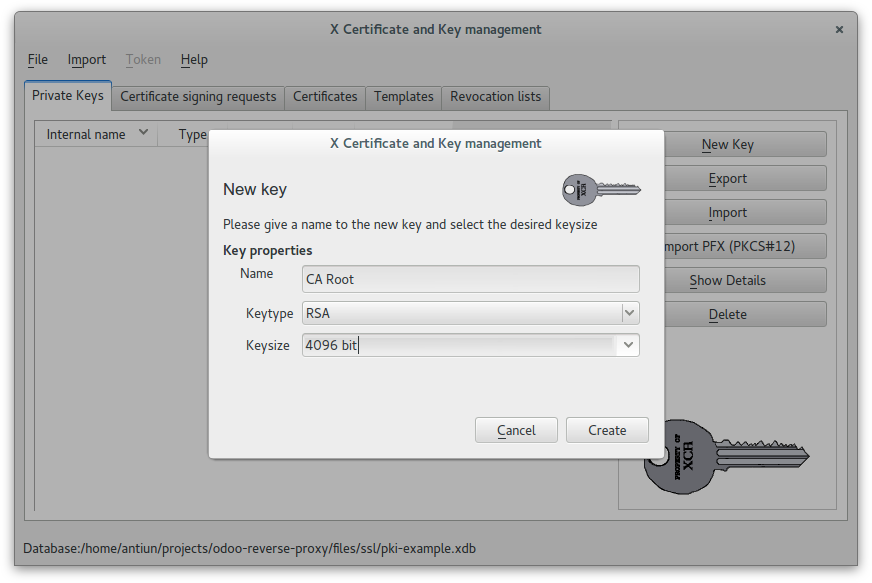
Create a 4096 RSA key for CA Root
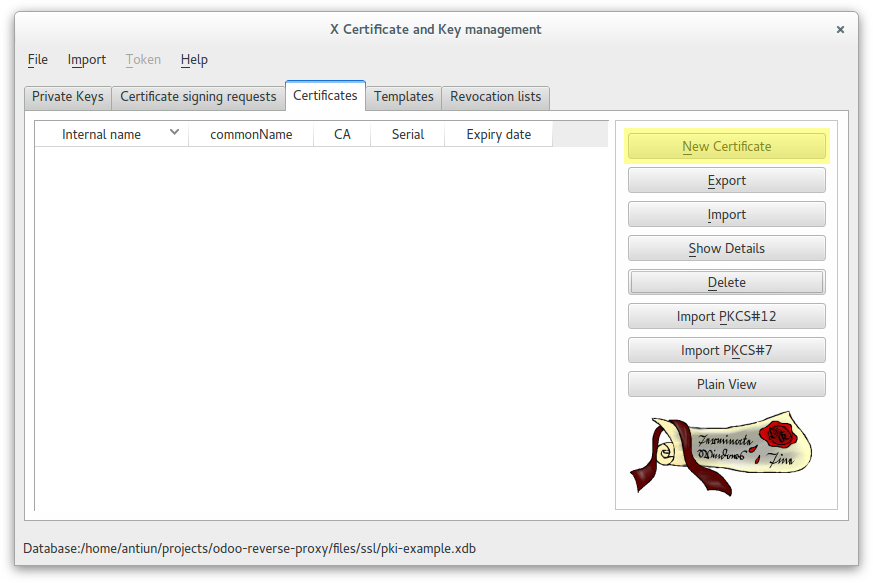
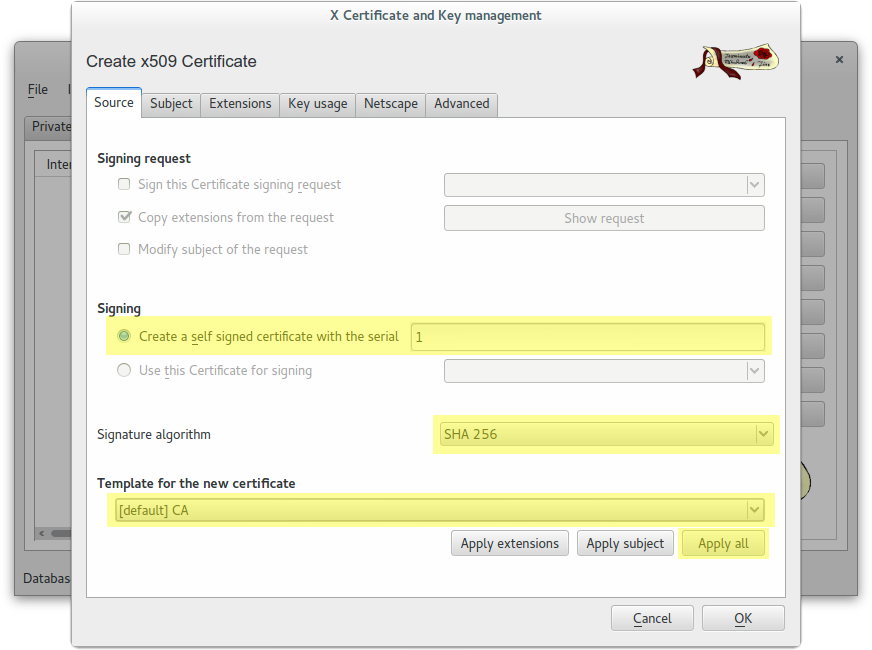
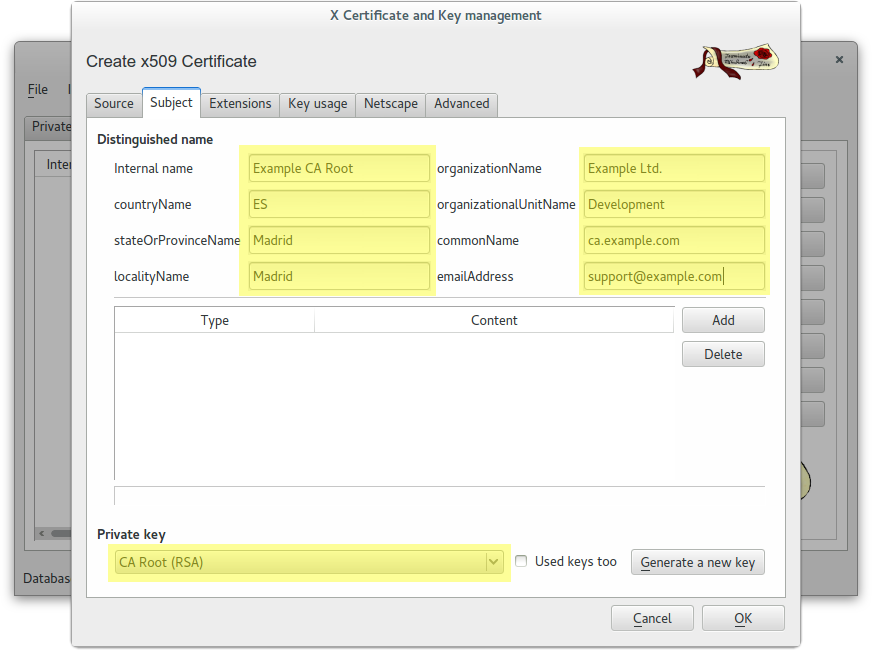
Create a self-signed CA Root certificate
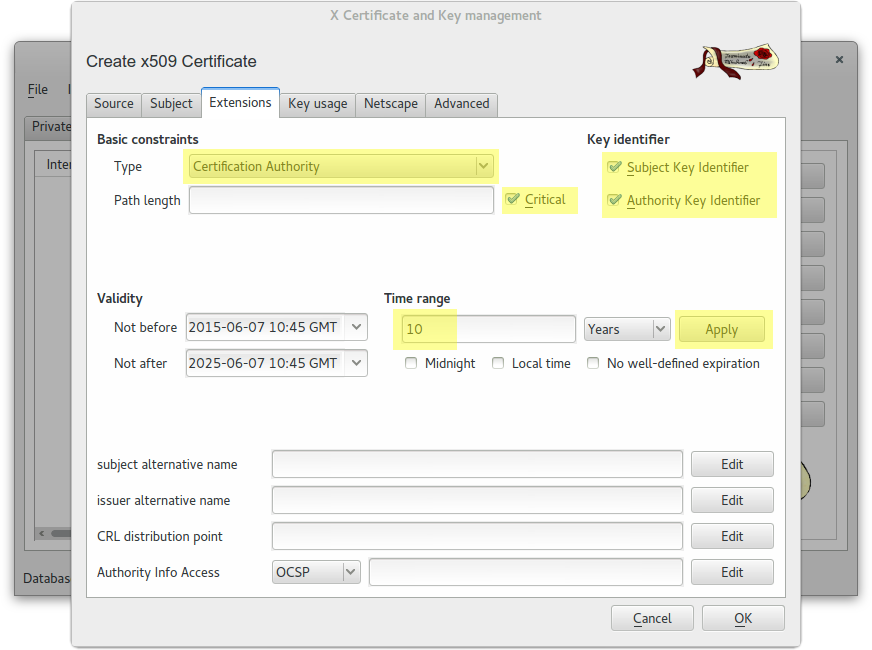
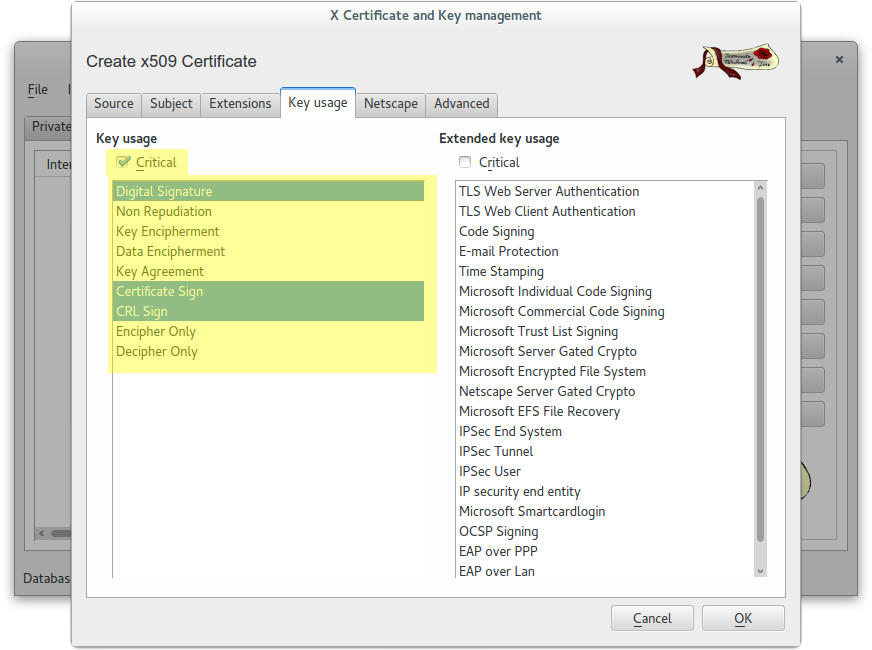
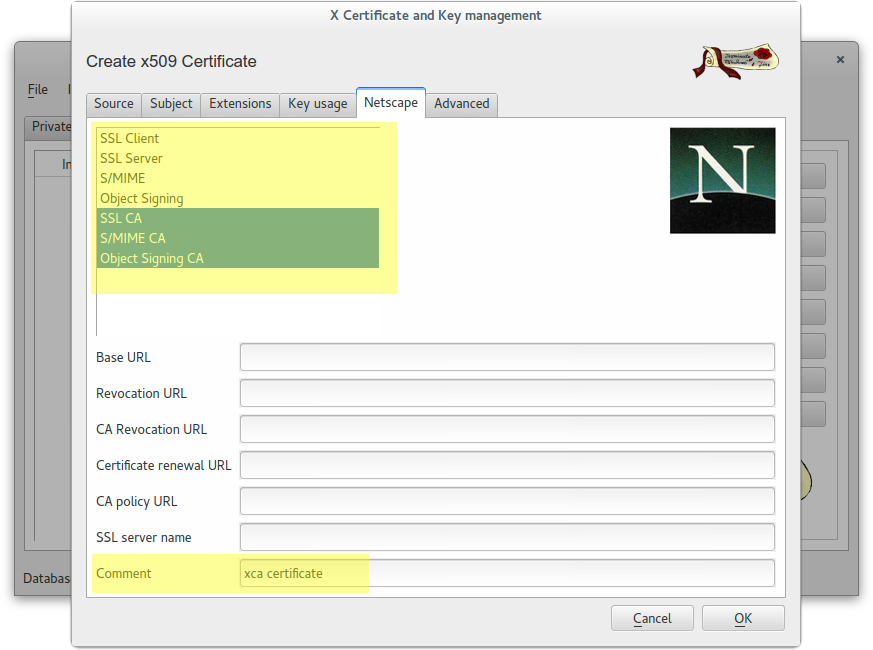
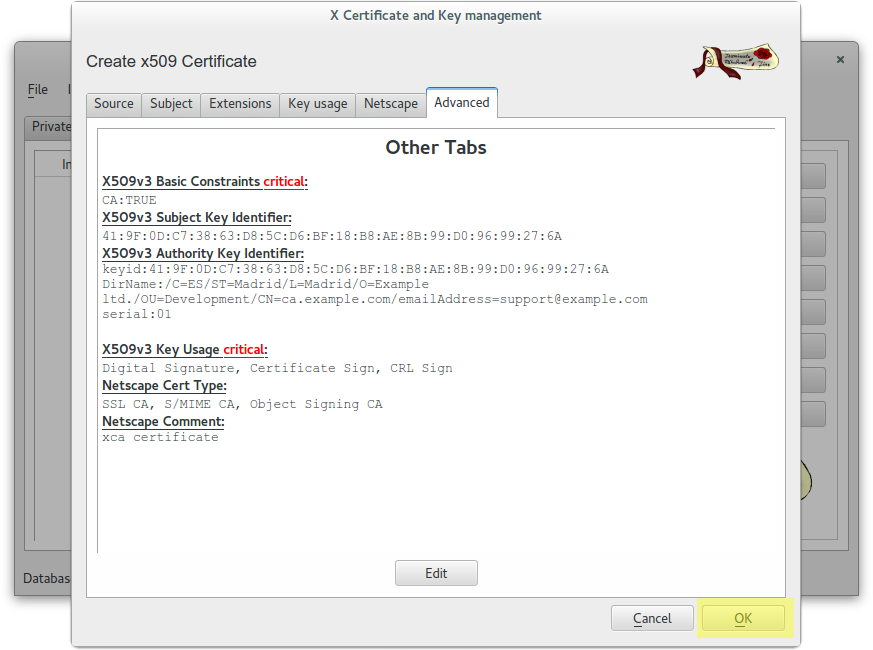
Create a wildcard certificate (*.example.com) signed by CA Root
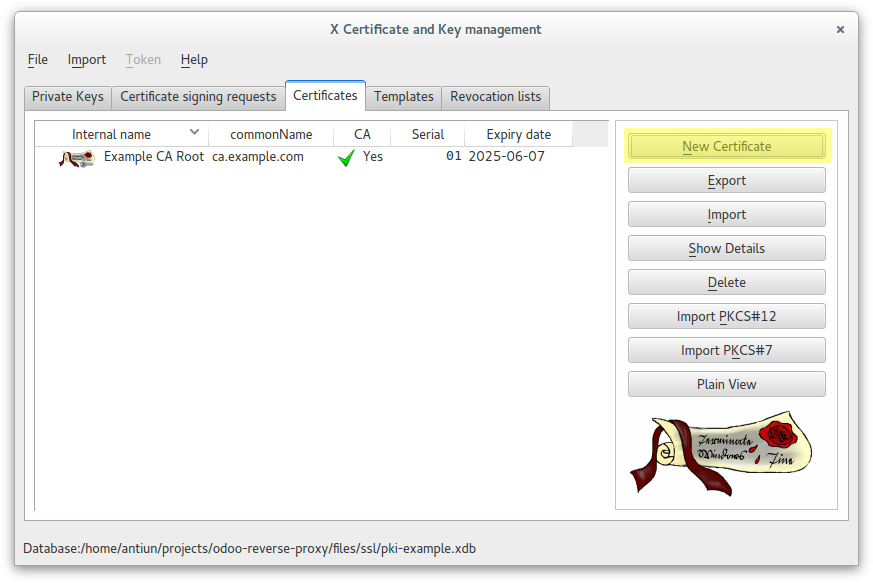
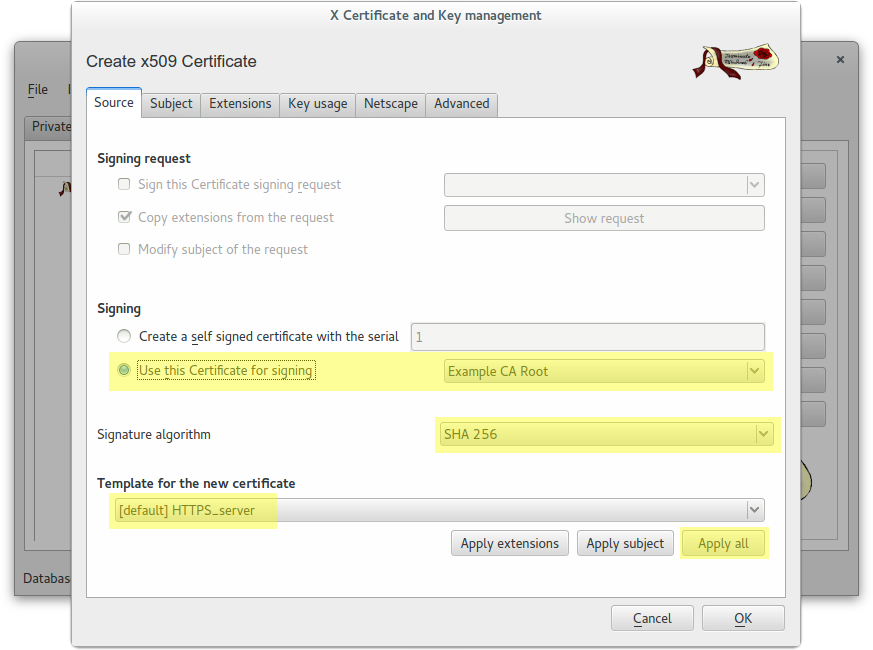
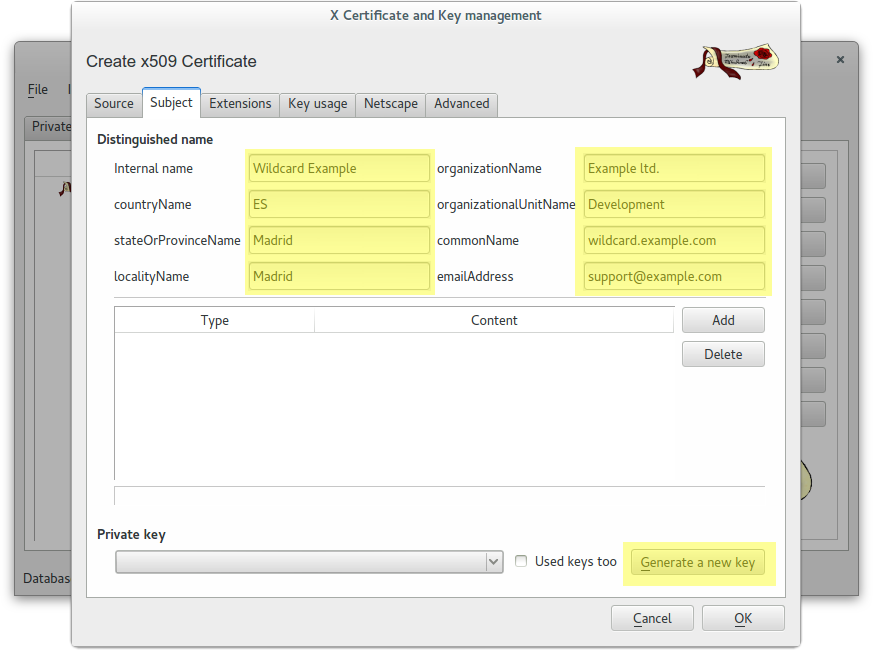
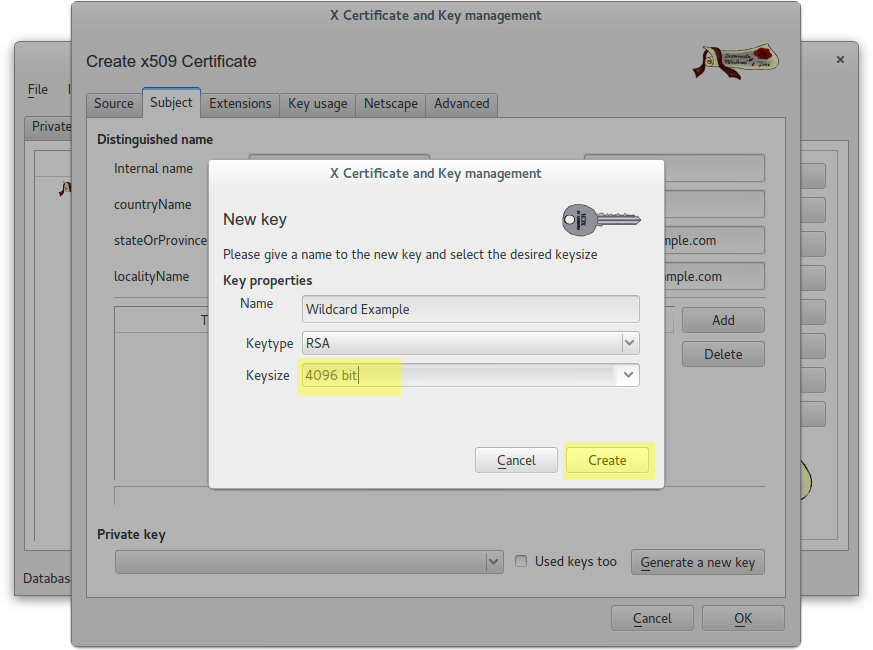
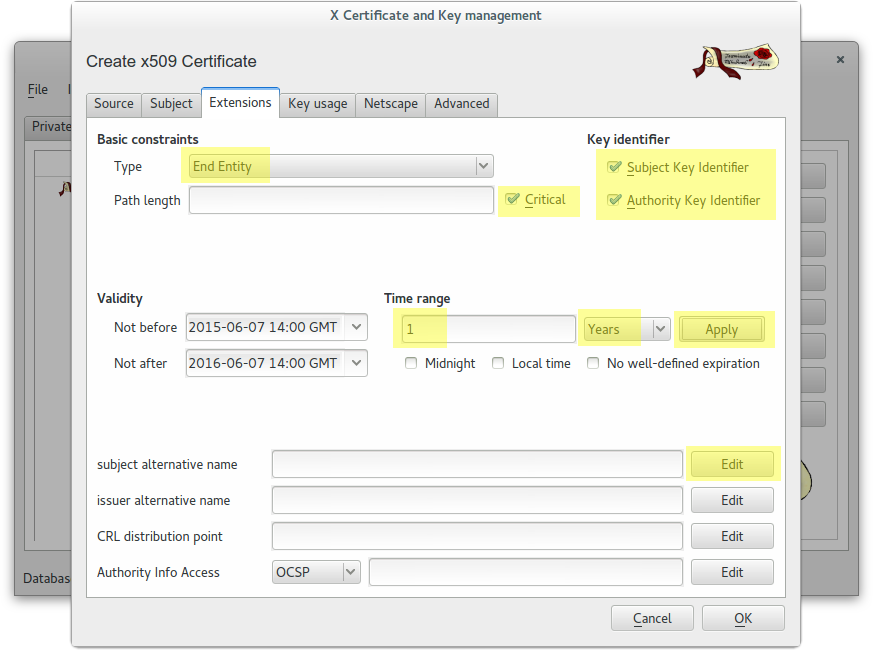
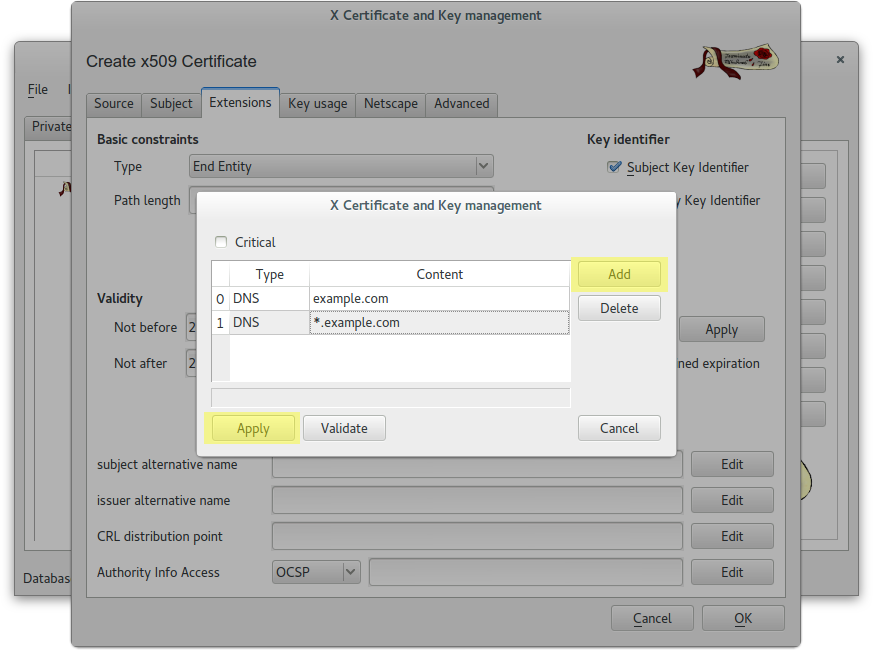
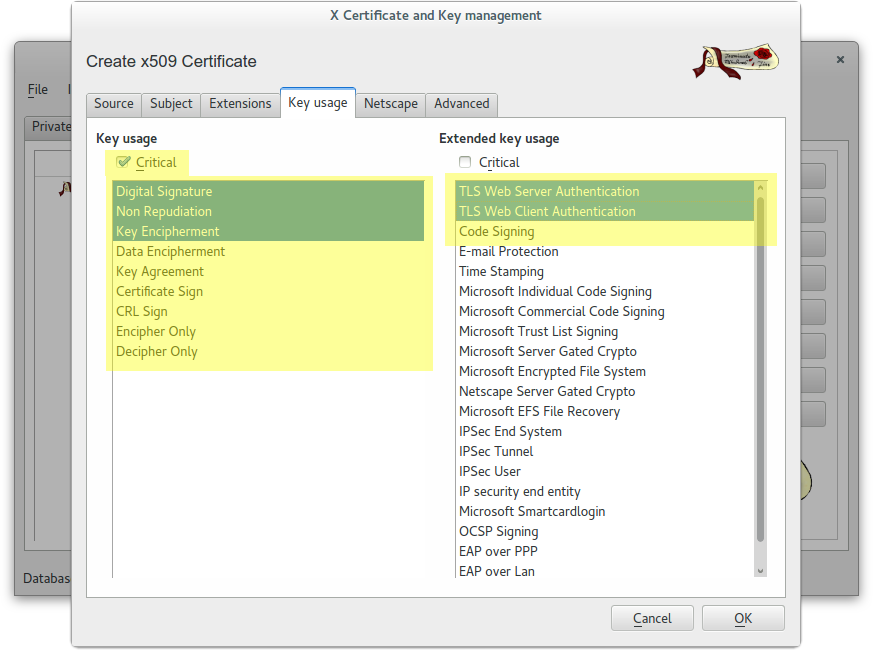
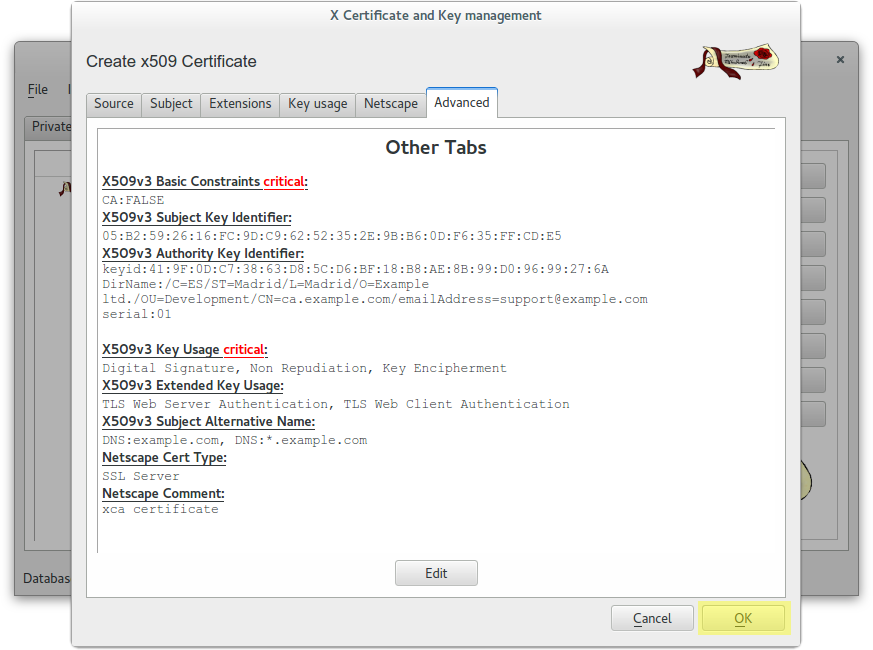
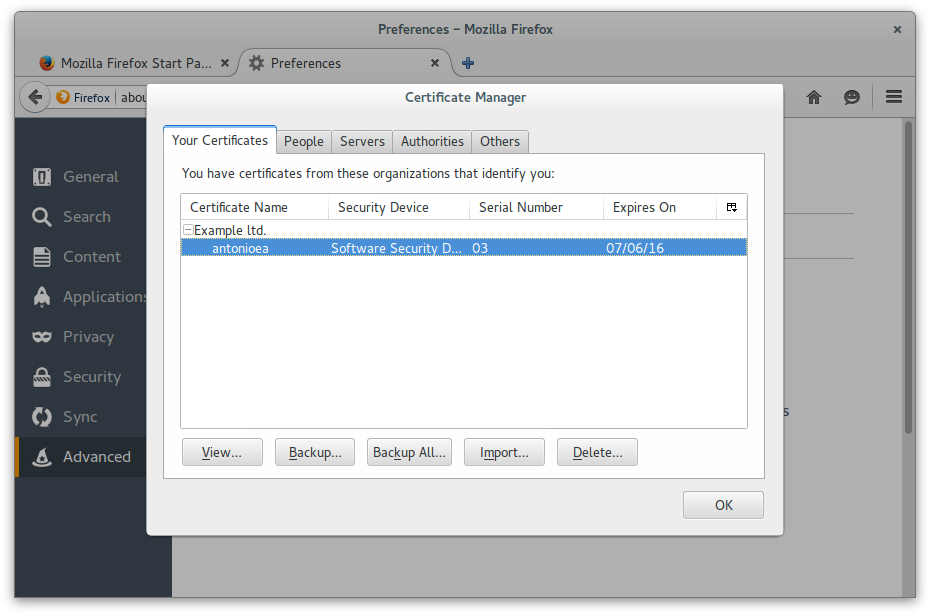
Create a client certificate (antonioea) signed by CA Root
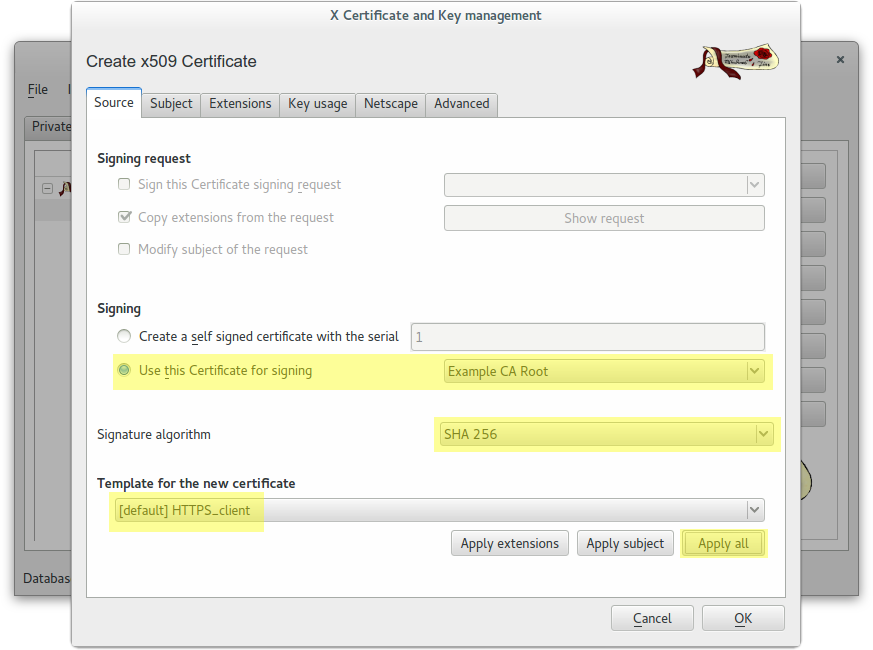
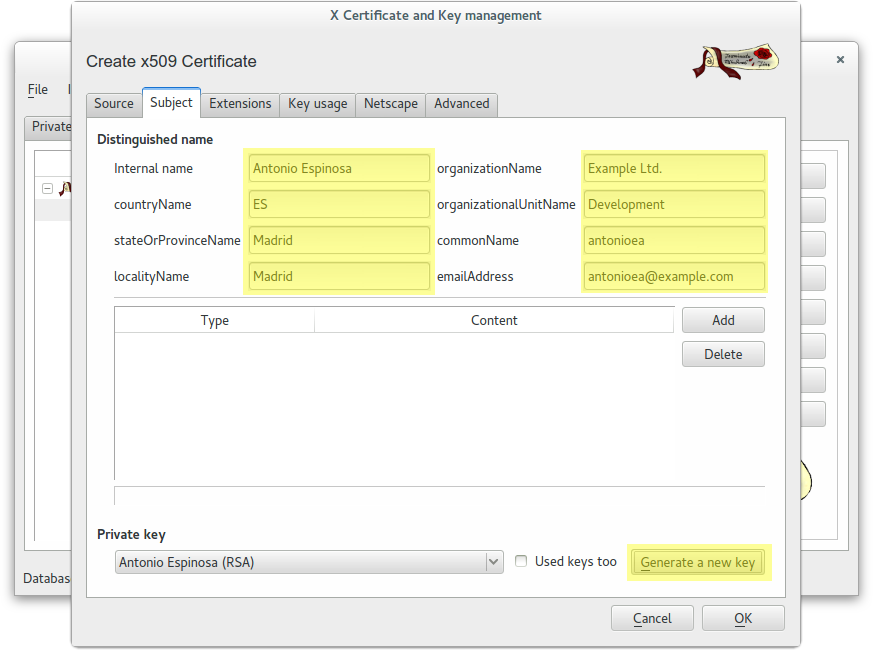
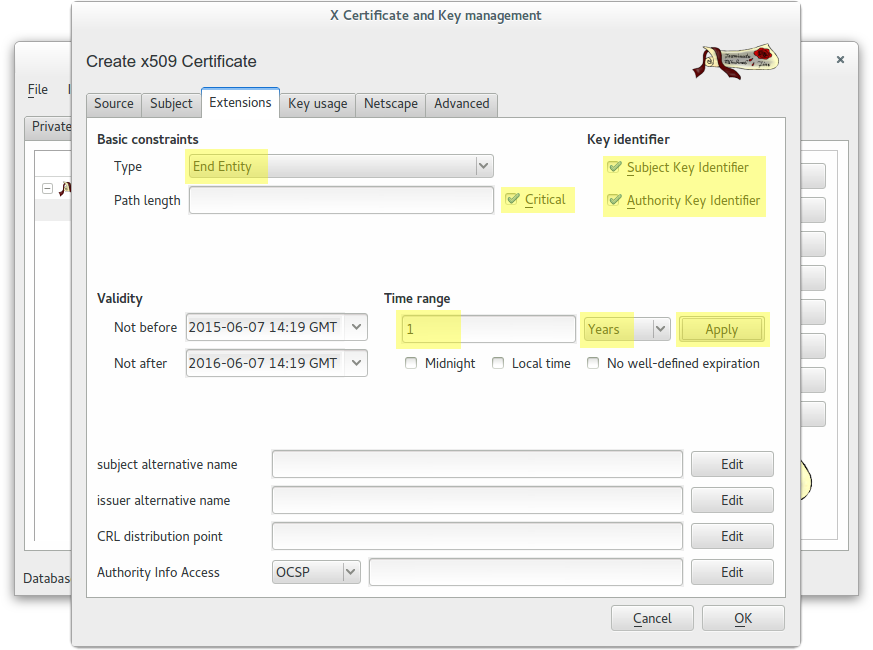
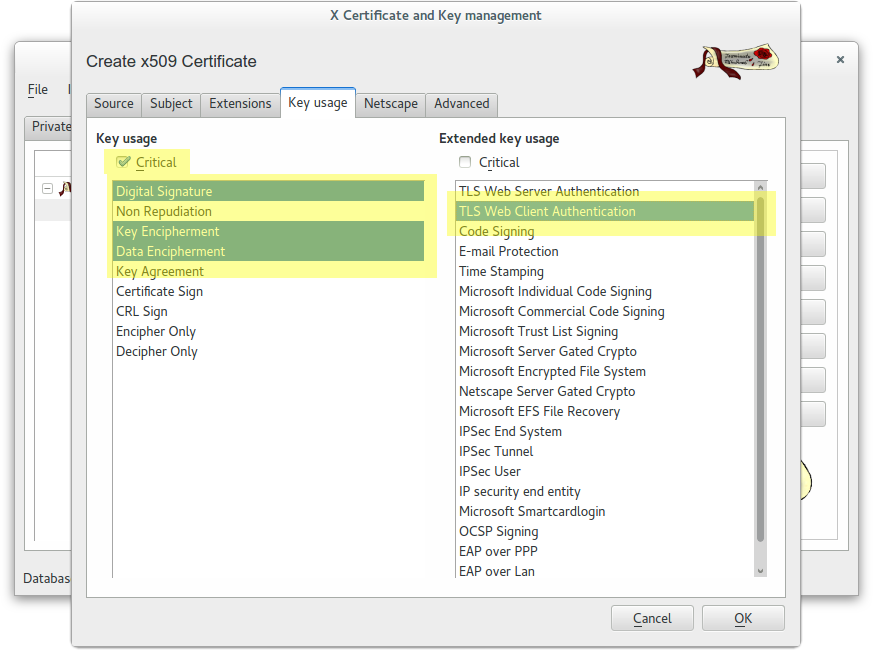
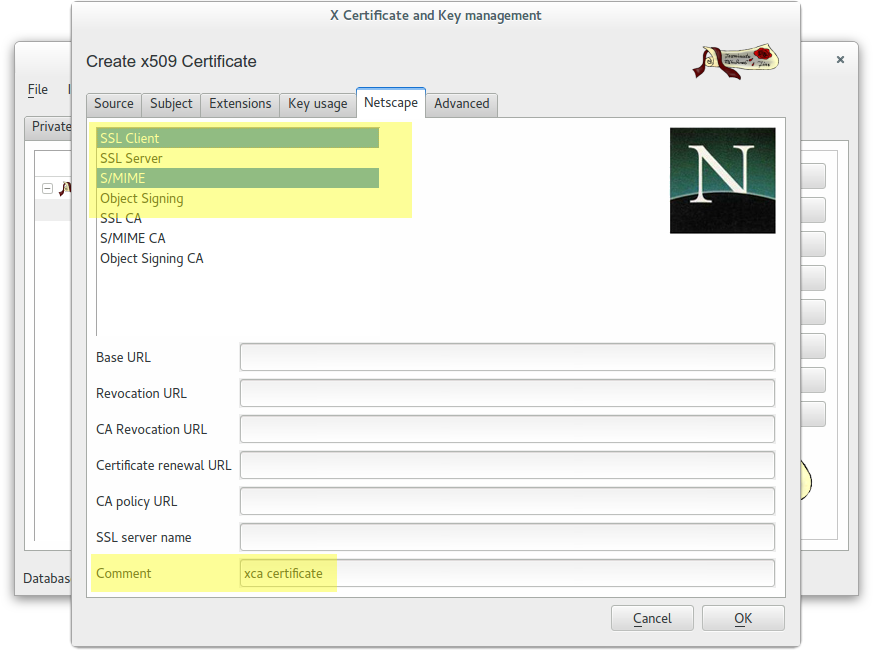
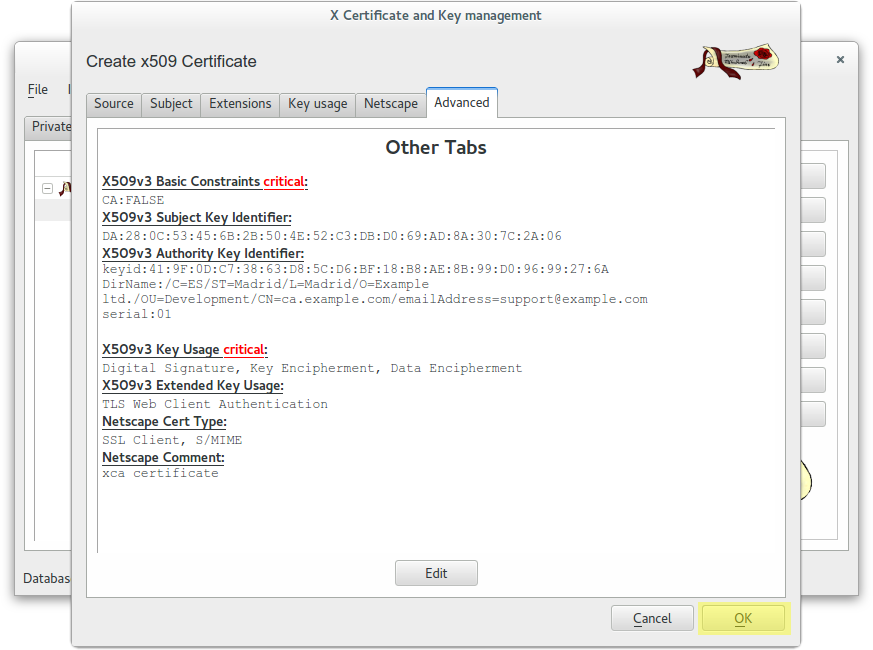
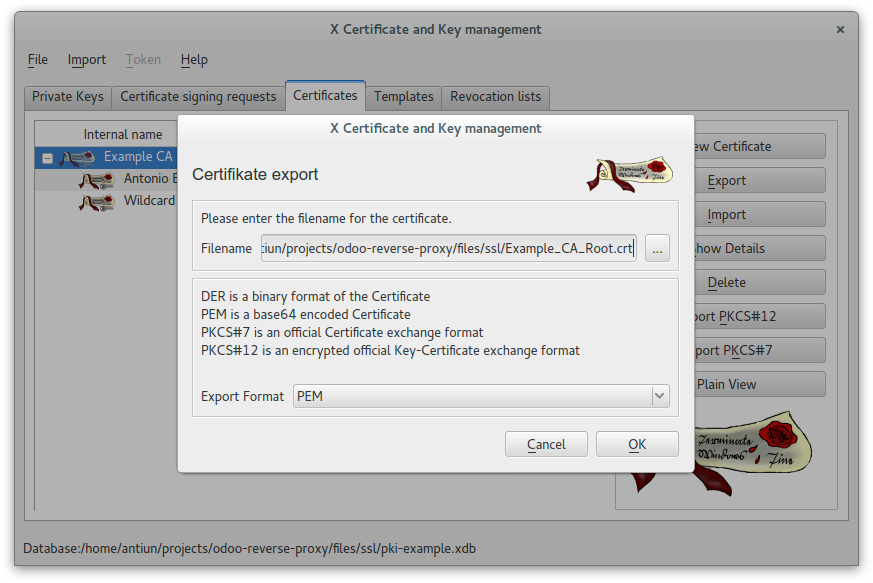
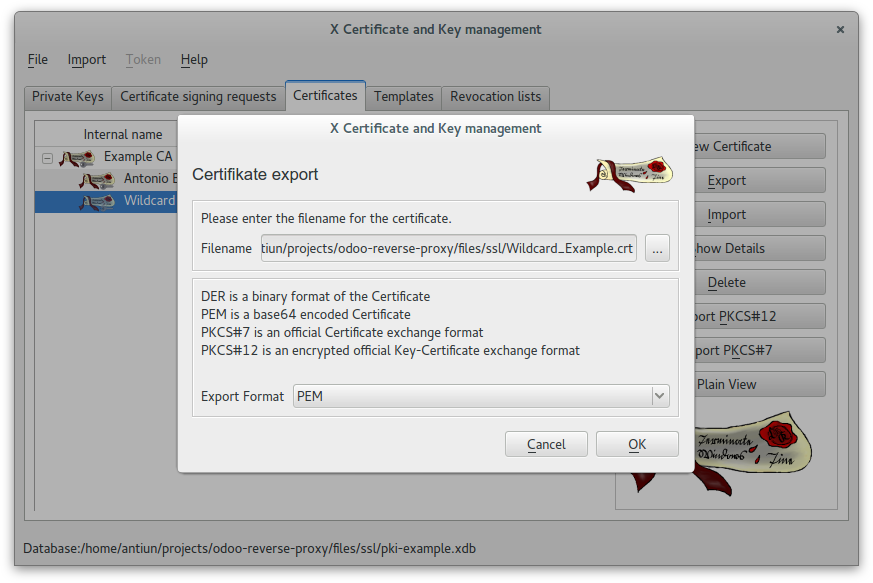
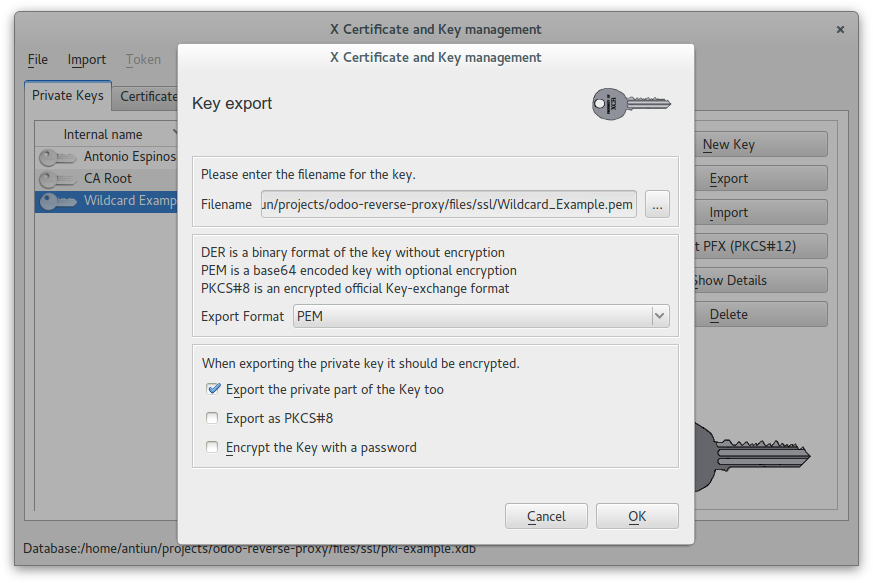
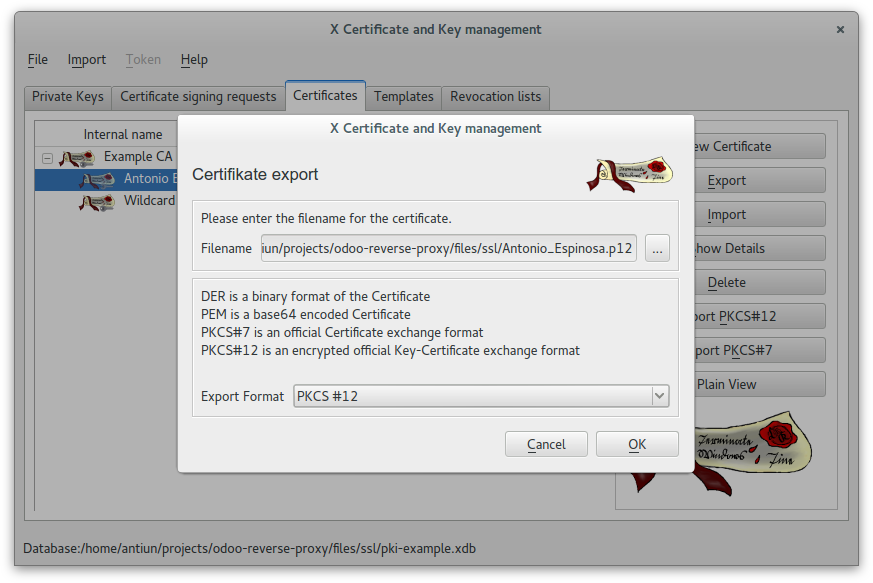
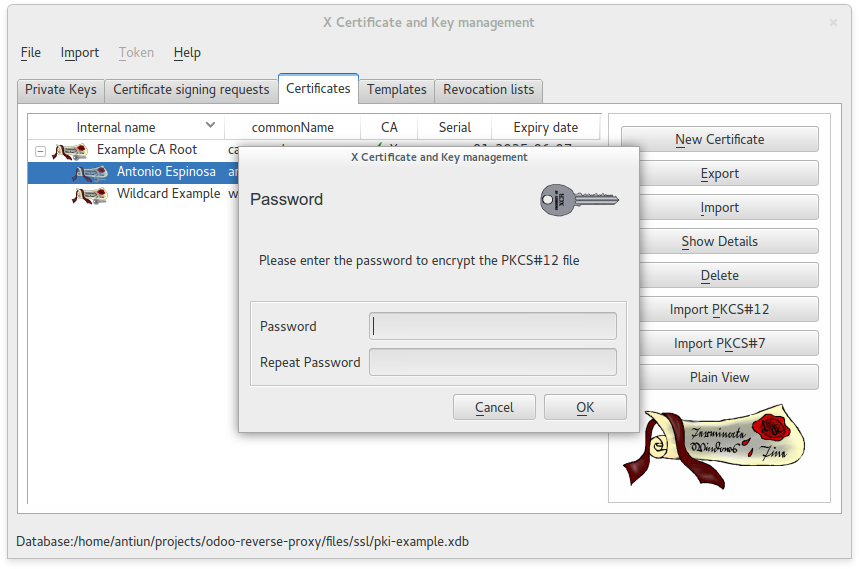
In this case we used this password: example
/usr/share/ca-certificates/example
Example_CA_Root.crt to /usr/share/ca-certificates/example/etc/ssl/wildcard.example.com
Wildcard_Example.crt to /etc/ssl/wildcard.example.comWildcard_Example.pem to /etc/ssl/wildcard.example.comProtect private key
sudo chmod 444 /usr/share/ca-certificates/example/Example_CA_Root.crt
sudo chmod 444 /etc/ssl/wildcard.example.com/Wildcard_Example.crt
sudo chmod 400 /etc/ssl/wildcard.example.com/Wildcard_Example.pemAdd Example CA Root as a trusted CA certificate
sudo nano /etc/ca-certificates.conf1 # (...)
2 example/Example_CA_Root.crtUpdate trusted CA certificates
sudo update-ca-certificates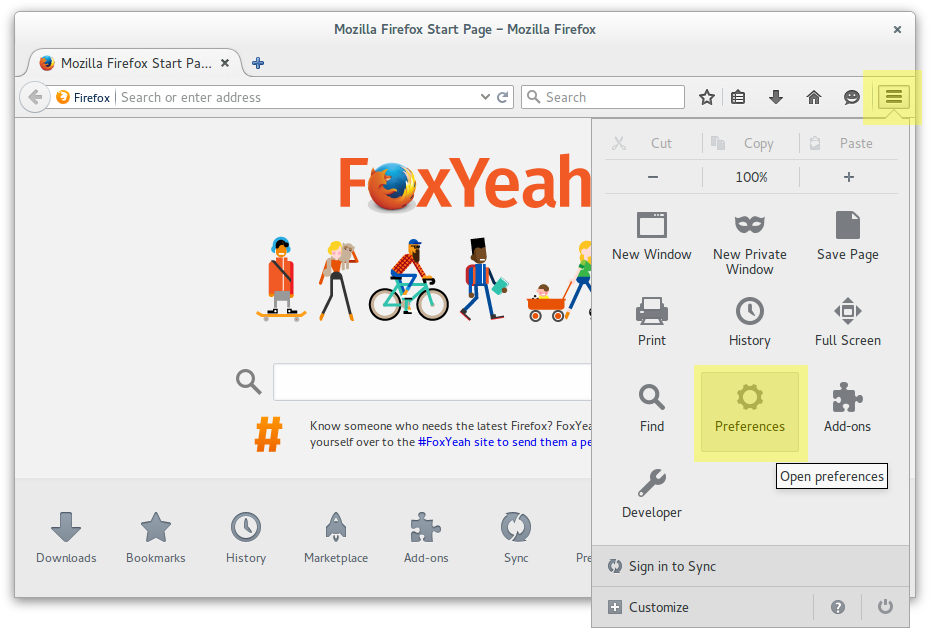
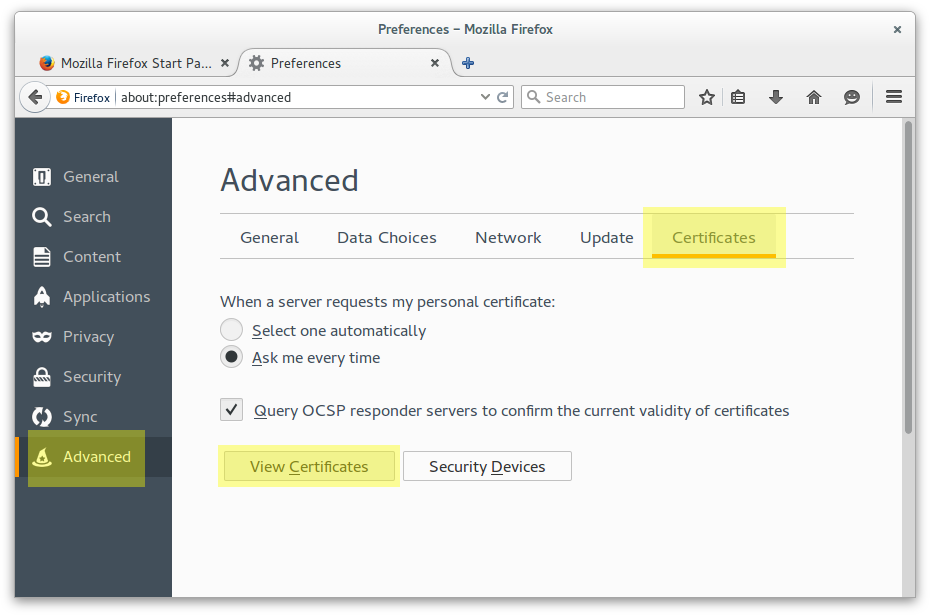
Add Example CA Root as a trusted Certification Authority
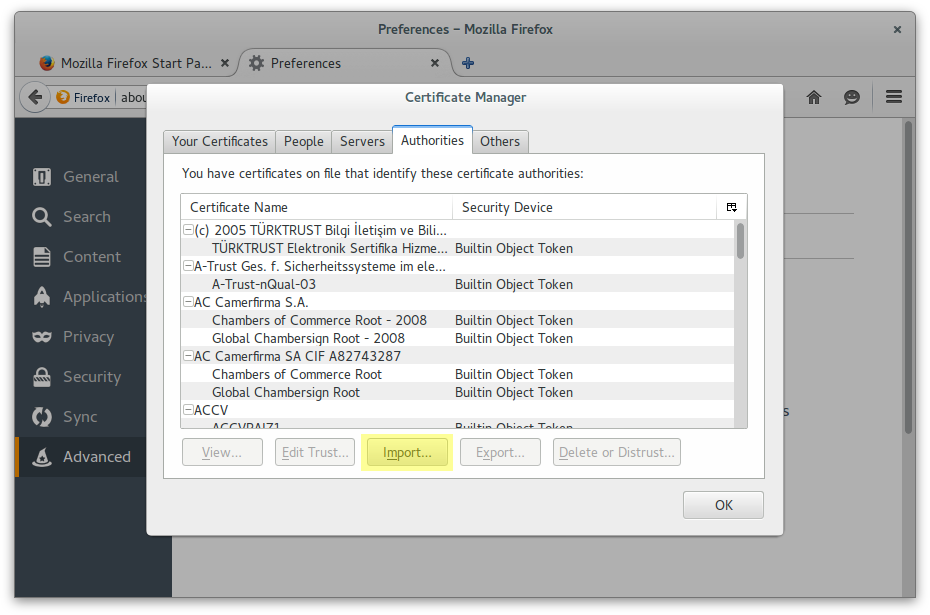
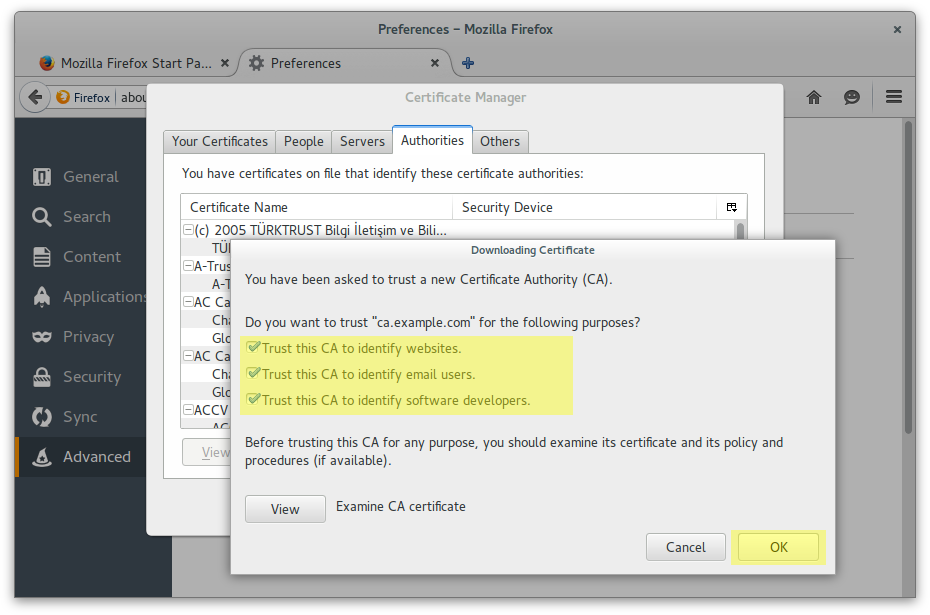
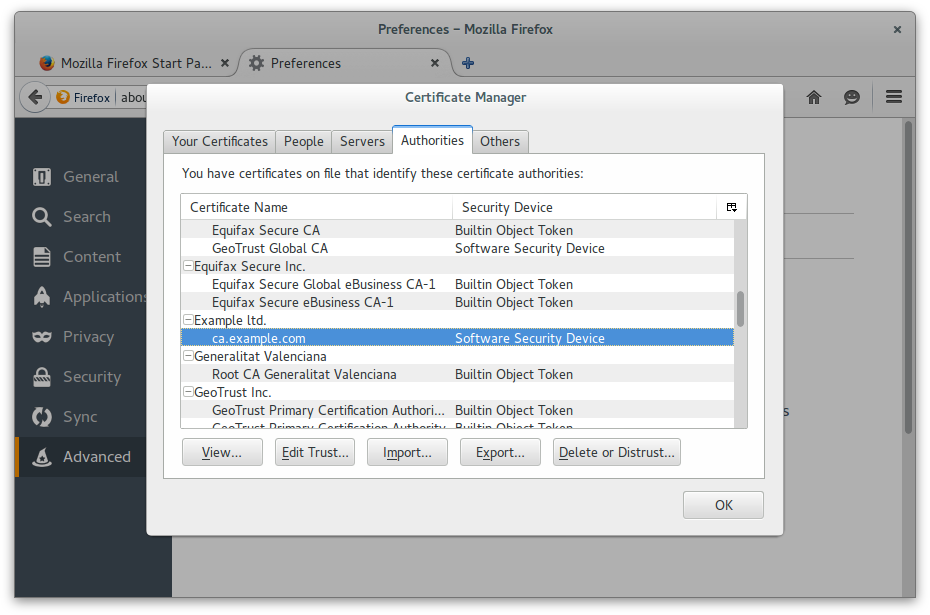
Add Antonio Espinosa as a personal certificate
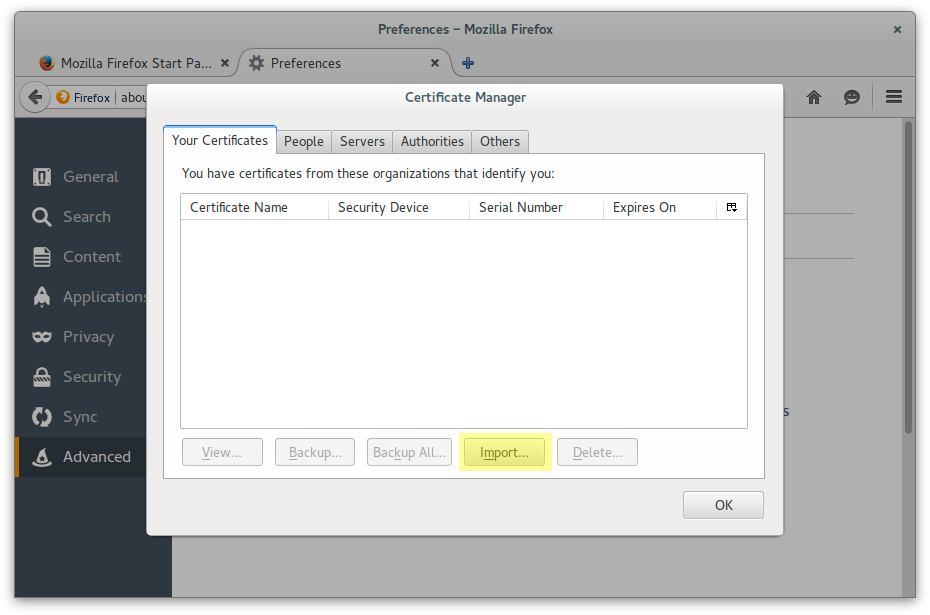
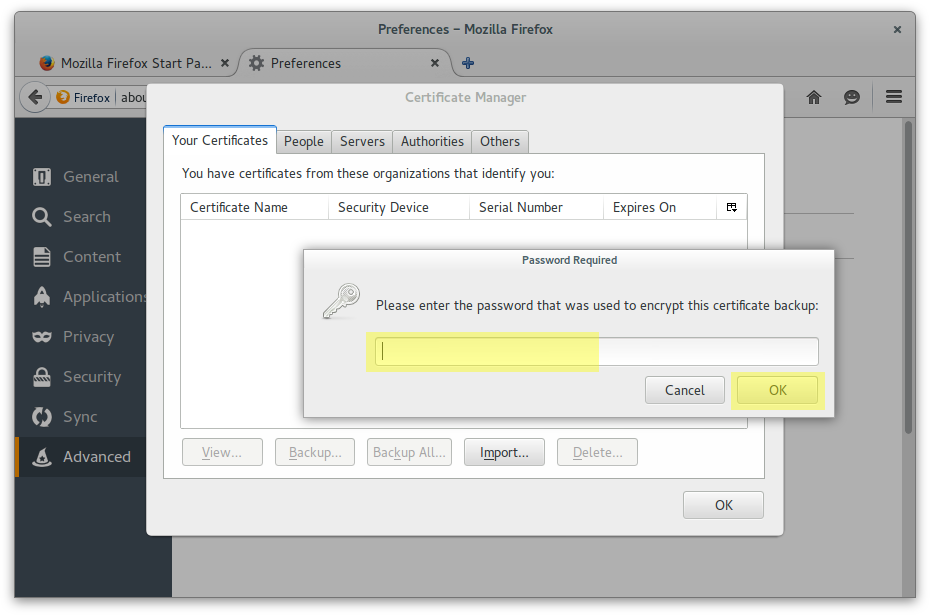

X-Forwarded-* headers through Werkzeug’s
proxy support.%h is replaced by the whole hostname the request is made on.%d is replaced by the subdomain the request is made on, with the
exception of www (so domain odoo.com and www.odoo.com both match the
database odoo)More options at Odoo Command-line interface
[options]
admin_passwd = admin
# Database configuration
db_host = localhost
db_port = False
db_user = odoo
db_password = odoo
# Ports to use
xmlrpc_port = 8069
longpolling_port = 8072
# Workers and timeouts
workers = 4
limit_time_real = 3600
limit_time_cpu = 3600
# Is it behind a HTTP reverse proxy?
proxy_mode = 1
# DB filtering for multi-site instances
dbfilter=^%h$sudo nano /etc/nginx/sites-available/odoo 1 server {
2 listen 80;
3 listen [::]:80 ipv6only=on;
4 server_name odoo.example.com;
5
6 # Strict Transport Security
7 add_header Strict-Transport-Security max-age=2592000;
8
9 # Redirect 301 to HTTPS
10 return 301 https://$host$request_uri;
11
12 access_log /var/log/nginx/default.access.log;
13 error_log /var/log/nginx/default.error.log;
14 }Download this file: odoo
sudo nano /etc/nginx/sites-available/odoo-ssl 1 upstream odoo {
2 server localhost:8069 weight=1 fail_timeout=3000s;
3 }
4
5 server {
6 listen 443;
7 listen [::]:443 ipv6only=on;
8 server_name odoo.example.com;
9
10 ssl on;
11 ssl_ciphers ALL:!ADH:!MD5:!EXPORT:!SSLv2:RC4+RSA:+HIGH:+MEDIUM;
12 ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
13 ssl_prefer_server_ciphers on;
14 ssl_certificate /etc/ssl/wildcard.example.com/public.crt;
15 ssl_certificate_key /etc/ssl/wildcard.example.com/private.pem;
16
17 # Specifies the maximum accepted body size of a client request,
18 # as indicated by the request header Content-Length.
19 client_max_body_size 200m;
20
21 # add ssl specific settings
22 keepalive_timeout 60;
23
24 # increase proxy buffer to handle some OpenERP web requests
25 proxy_buffers 16 64k;
26 proxy_buffer_size 128k;(…)
Download this file: odoo-ssl
(…)
1 location / {
2 proxy_pass http://odoo;
3
4 # Force timeouts if the backend dies
5 proxy_next_upstream error timeout invalid_header http_500 http_502 http_503;
6
7 # Set headers
8 proxy_set_header Host $host;
9 proxy_set_header X-Real-IP $remote_addr;
10 proxy_set_header X-Forward-For $proxy_add_x_forwarded_for;
11 # Let the Odoo web service know that we're using HTTPS, otherwise
12 # it will generate URL using http:// and not https://
13 proxy_set_header X-Forwarded-Proto https;
14
15 # Set timeouts
16 proxy_connect_timeout 3600;
17 proxy_send_timeout 3600;
18 proxy_read_timeout 3600;
19 send_timeout 3600;
20
21 # By default, do not forward anything
22 proxy_redirect off;
23 }
24 }(…)
Download this file: odoo-ssl
(…)
1 # Cache some static data in memory for 60mins.
2 # under heavy load this should relieve stress on the Odoo web interface a bit.
3 location ~* /[0-9a-zA-Z_]*/static/ {
4 proxy_cache_valid 200 60m;
5 proxy_buffering on;
6 expires 864000;
7 proxy_pass http://odoo;
8 }
9
10 access_log /var/log/nginx/odoo-ssl.access.log;
11 error_log /var/log/nginx/odoo-ssl.error.log;
12 }Download this file: odoo-ssl
cd /etc/nginx/sites-enabled
rm -rf *
ln -s ../sites-available/odoo odoo
ln -s ../sites-available/odoo-ssl odoo-ssl
service nginx restart[options]
admin_passwd = admin
# Database configuration
db_host = localhost
db_port = False
db_user = odoo
db_password = odoo
# Ports to use
xmlrpc_port = 8069
longpolling_port = 8072
# Workers and timeouts
workers = 4
limit_time_real = 3600
limit_time_cpu = 3600
# Is it behind a HTTP reverse proxy?
proxy_mode = 1
# DB filtering for multi-site instances
dbfilter=^%h$sudo nano /etc/apache2/sites-available/odoo.conf 1 <VirtualHost *:80>
2 ServerAdmin webmaster@example.com
3 ServerName odoo.example.com
4
5 <IfModule mod_rewrite.c>
6 RewriteEngine On
7
8 # Permanent redirect (301 HTTP) if no canonical domain name
9 RewriteCond %{HTTP_HOST} !^odoo.example.com
10 RewriteRule ^/(.*)$ http://odoo.example.com/$1 [R=301,NE,L]
11
12 # Redirect 301 to HTTPS
13 RewriteCond %{HTTPS} !=on
14 RewriteRule ^/?(.*) https://%{SERVER_NAME}/$1 [R=301,NE,L]
15 </IfModule>
16
17 <Location "/" >
18 Order deny,allow
19 Deny from all
20 Allow from all
21 </Location>
22
23 ErrorLog /var/log/apache2/odoo.example.com.error.log
24 LogLevel warn
25 CustomLog /var/log/apache2/odoo.example.com.access.log combined
26
27 </VirtualHost>Download this file: odoo
sudo nano /etc/apache2/sites-available/default-ssl.conf 1 <VirtualHost *:443>
2 ServerAdmin webmaster@example.com
3 ServerName odoo.example.com
4
5 SSLEngine on
6 SSLProtocol all -SSLv2 -SSLv3
7 SSLCipherSuite ALL:!ADH:!EXPORT:!SSLv2:RC4+RSA:+HIGH:+MEDIUM
8 SSLCertificateFile /etc/ssl/wildcard.example.com/public.crt
9 SSLCertificateKeyFile /etc/ssl/wildcard.example.com/private.pem
10
11 RequestHeader set X-Forwarded-Proto "https"
12
13 <IfModule mod_rewrite.c>
14 RewriteEngine On
15
16 # Permanent redirect (301 HTTP) if no canonical domain name
17 RewriteCond %{HTTP_HOST} !^odoo.example.com
18 RewriteRule ^/(.*)$ https://odoo.example.com/$1 [R=301,NE,L]
19 </IfModule>(…)
Download this file: odoo-ssl.conf
(…)
1 <Location "/" >
2 Order deny,allow
3 Deny from all
4 Allow from all
5 </Location>
6
7 <Location "/web/database/manager" >
8 Order deny,allow
9 Deny from all
10 Allow from 192.168.122.0/24 127.0.0.0/255.0.0.0 ::1/128
11 </Location>
12
13 <Location "/website/info" >
14 Order deny,allow
15 Deny from all
16 Allow from 192.168.122.0/24 127.0.0.0/255.0.0.0 ::1/128
17 </Location>(…)
Download this file: odoo-ssl.conf
(…)
1 # Comment to disable proxy
2 ProxyRequests Off
3 ProxyPreserveHost On
4 ProxyPass /longpolling/ http://localhost:8072/longpolling/ retry=0
5 ProxyPassReverse /longpolling/ http://localhost:8072/longpolling/ retry=0
6 ProxyPass / http://localhost:8069/ retry=0
7 ProxyPassReverse / http://localhost:8069/ retry=0
8
9 ErrorLog /var/log/apache2/odoo.example.com-ssl.error.log
10 LogLevel warn
11 CustomLog /var/log/apache2/odoo.example.com-ssl.access.log combined
12
13 </VirtualHost>
14 </IfModule>Download this file: odoo-ssl.conf
cd /etc/apache2/sites-enabled
rm -rf *
ln -s ../sites-available/odoo.conf 010-odoo.conf
ln -s ../sites-available/odoo-ssl.conf 010-odoo-ssl.conf
service apache2 restartSSLVerifyClient none
SSLCACertificateFile /usr/share/ca-certificates/example/Example_CA_Root.crt
<Location "/" >
Order deny,allow
Deny from all
Allow from all
</Location>
<Location "/web/database/manager" >
SSLVerifyClient require
SSLVerifyDepth 10
SSLRequireSSL
SSLRequire %{SSL_CLIENT_S_DN_O} eq "Example Ltd." and
%{SSL_CLIENT_S_DN_OU} in {"Development"}
</Location>
<Location "/website/info" >
SSLVerifyClient require
SSLVerifyDepth 10
SSLRequireSSL
SSLRequire %{SSL_CLIENT_S_DN_O} eq "Example Ltd." and
%{SSL_CLIENT_S_DN_OU} in {"Development"}
</Location>
![]() Antonio Espinosa
Antonio Espinosa
Twitter
Github personal
 Antiun Ingeniería
Antiun Ingeniería
www.antiun.com
Github - Antiun addons
/
#